WINDOWS NT 4.0 -- TECHNICAL SUPPORT
Chapter 4: Managing System Policies
Chapter 5: Managing File Systems
Chapter 6: Managing Partitions
Chapter 7: Managing Fault Tolerance
Chapter 8: Supporting Applications
Chapter 15: Implementing Network Clients
- The Purpose of System Pocicies
- Implementing a System Policy
- Using System Policy Editor to Manage a System Policy
- Key Points
System policies override local registry values for user or computer settings, to enable administrator to control individual desktop and registry settings.
A system policy is made up of computer policy, user policy, group policy, or any combination of these policies -- each one is in fact an entry in a same system policy file (NTconfig.pol) , NOT separate files.
Using System Policy Editor (poledit.exe or in the Administrator Tools (common) menu) to restrict or configure users desktop settings -- to control user-defined settings in user profiles and to change system configuration settings. When a system policy is used in a domain, it can establish a uniform set of rules, or policy, for all users and NT or Windows 95 computers. System policy can also be configured to provide custom desktop and computer configurations for specific users, and computers.
System Policy Editor only available with NT Server, not in NT Workstation. Windows 95 has its own System Policy Editor.
Only administrators can create and change system policies.
Computer Policy and User Policy
Computer Policy -- configure logon and network settings. The default computer policy applys to all computers in the domain and effect all users that log on those computers.
Use Edit >> Add Computer... to customize a specific computer policy.
User Policy -- configure user's desktop. The default user policy effects all users that log on to the domain.
Use Edit >> Add User... or >> Add Group... to customize a specific user policy.
Note: System Policy Editor is in NT Server only !
To create a new policy for a domain
1. File >> New Policy
2. To specify the computers to which your Registry-setting changes will apply, you can do the following:
- >>Default User -- to change HKEY_CURRENT_USER Registry settings for all computers on the domain.
- >>Default Computer -- to change HKEY_LOCAL_MACHINE Registry settings for all computers on the domain.
3. To add to the Registry settings, click Commands on the Edit menu to do the following:
- >>Add User -- to change HKEY_CURRENT_USER for specific users
- >>Add Computer -- to change HKEY_LOCAL_MACHINE for specific computers.
- >>Add Group -- to change HKEY_CURRENT_USER for specific groups.
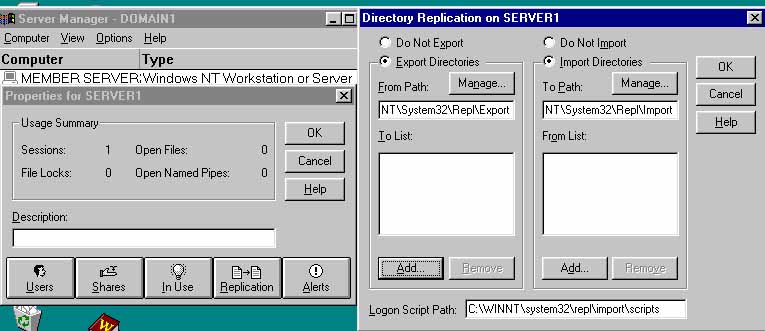
4. >>File >>Save As -- Ntconfig.pol on the PDC in the Netlogon folder:
- systemroot\System32\Repl\Import\Scripts
(note Netlogon is in the Import folder!?)
On domain controllers, NT installation automatically shares this folder as Netlogon
5. Use Server Manager to enable Replication services on all domain controllers so that the Ntconfig.pol file is replicated to the same folder on all BDCs.
User Policy:
User Policy Specific to the logged_on_User >>Group Policy (only when this user is a member of these groups) >> Default User Policy
- + Computer policy: (has higher priority over User Policy)
Computer Policy specified for this computer >> Default Computer policy
Note: Policies are applied ONLY at the time a user log on. If a user is logged on when a system policy change is implemented, the user must log off and log back on for the policy to take effect.
System Policy for Windows 95 -- to apply system policies in a network that uses both Window 95 and NT Workstation, you have to use Win95's System Policy Editor to make a system policy for Win95 clients, and must name the policy file Config.pol (similar to Ntconfig.pol, but in different file format and reflects differences in the registries of the two operating systems), and must also save it to the Netlogon share on the PDC.
Implementing a Local Policy -- for NT computers to access system policy from a non-DC computer)
This is a direct edit portions of the local registry and changes are reflected almost immediately. This mode exposes certain keys in HKEY_CURRENT_USER and HKEY_LOCAL_MACHINE. The user does not need to log off or restart the computer to see the changes!
Note:
When using the registry mode, you're making changes to the registry directly (of an individual local or remote computer only); you're NOT editing the system policy file (Ntconfig.pol) -- that is what Policy Mode does!
To simplifying administration, AVOID using Registry Mode to change individual computer registry settings. If a specific user or computer needs different settings, the best way is to simply create a separate policy entry (by >> Add User /Group/Computer) within the domain system policy (Ntconfig.pol)
Policy mode is used to create or modify system policy files (.pol). Changes made are not implemented until all the following procedures are completed:
Users log on to the domain (if currently logged on, has to log off and then log on again?)
The default settings (Default User and Default Computer) can affect the entire domain. To customize System Policy for Users, Groups, and Computers, use the Policy mode >>Edit >> Add User or >>Add Group, or >>Add Computer, to let them have separate entries in the Ntconfig.pol file.
For Windows 95 computer --
System policies can only be stored on DCs (while NT computer can be configured to use system policy file on computers other than DCs). Besides, by default, Windows 95 computer get policy settings from the PDC only.
You can install/enable group policies on Win95 --
or after Windows 95 installation, by using >>Control Panel >>Add/Remove Programs
system_root\System32\Import\Scripts
Remember that system policy file created on NT Server cannot be used on Windows 95, and vice versa.
In other words, for Windows 95 computers access Config.pol on BDCs, load balancing must be enabled on these computers running Windows 95.
How to enable load balancing --
use Windows 95 System Policy Editor >> open Config.pol >> Default Computer >>Network \Update \Remote Update Policy >> check Load-balanced
Downloading system policies is very slow
-- On NT computers, set Computer Policy >> Remote update >> Manual, and use computers other than the DCs to store the system policy files.
Note: to help reduce network traffic, for Win95 computers, let them get policy form other DCs than the PDC by setting Load Balance; for NT computers, let them get policy from a non-DC computer (can be themselve) by implementing a local policy.
Windows NT and 95 use different system policy file names, and they are NOT interoperable (in different format). You must create a user policy in both system policy files -- Config.pol for 95, and Ntconfig.pol for NT; however, they are in the same folder -- the Ntlogon share.
System policies can ONLY
restrict access to Control Panel options,
but cannot remove
the icons.
To remove the icons from Control Panel,
modify the [don't load] section of Control.ini
Some system policy settings require components to be installed locally on the computer where the policy is applied. In this example, the wallpaper bitmap is not present in the path specified by the policy file.
Options >>Group Priority >>Click a group in Group Order >>Move Up or Move Down.
Groups highest on the list have the highest priority.
Note --The order in which groups are evaluated is important if some users belong to more than one group for which policy is defined and if the policy settings in two or more of these groups contain different settings for the same policy. To specify which policy has priority, use Group Order to order the groups.
File >> Connect >>type the name of the remote computer >>in the Users on Remote Computer dialog box, click the user that is interactively logged on >>OK
- >> Local User -- to change HKEY_CURRENT_USER Registry settings.
- >> Local Computer -- to change HKEY_LOCAL_MACHINE Registry settings.
- then >>File >>Save >>File >> Disconnect
Note: You can access the Registry only on computers for which you have administrative permission. The computer can be running any version of Windows NT Workstation or Windows NT Server.
While at the individual computer:
>>File >>Open Registry, Or, >>File >>Connect >>specify a computer name.
>>Default Computer >>Network >>System policies update >>Remote update >>to have registry process error messages displayed on client computers -->>Display error messages.
to download the policy file from a server other than domain controllers -->>Manual (use specific path) in Update mode, and then provide the specific path.
>> save the policy files in the appropriate folder.
Note: You can access the Registry only on computers for which you have administrative permission.
A system policy is made up of comupter policy, user policy, group policy, or any combination of these policies
By default, to implement a domain system policy on NT computers, the policy settings must be stored in a file named Ntconfig.pol in the Netlogon share of the PDC. Which was then replicated (and thus available in) to all DCs.
By default, all NT computers automatically download the info in the Ntconfig.pol in a DC that authenticated the logon request. You can have an NT computer use a local system policy from a non-DC computer, by changing the Remote Updata settings (in Computer Policy>>Network) to manual and specify the path to the computer and the system policy file.
For Win95 computers, use its own System Policy Editor, name the system policy file Config.pol, and must save it also in the Ntlogon share on the PDC.
If implementing group policies for Win95 clients, Group Policies must be installed/enabled on each Win 95 computer -- not only to create group policies, but to process them. (Unlike NT, Group Policies are not installed by default with System Policy Editor on Win95).
Both Ntconfig.pol and Config.pol must be stored on the PDC in the folder: system_root\sytem32\Repl\Import\Scripts -- which by default is shared as Netlogon.
Replication must be enabled for all DCs to receive copies of the Ntconfig.pol and Config.pol. Also, load balancing must be enabled on Win95 computers in order for them to access the Config.pol on BDCs (otherwise, they can access the policy file on the PDC only). To enable load balancing, modify the Config.pol with Win95's Policy Editor.
System Policy Editor can be used to directly edit portions of the registry (when in the Registry Mode)
- File system support by NT
- Working with File Names
- Managing NTFS compression
- Key Points
FAT16, NTFS, and CDFS (read-only).
Note: NT 4.0 or older cannot access FAT32.
More FAT Features / Considerations:
More NTFS Features / Considerations:
Note: Though POSIX application can be run from any NT file system, when the application requires to access file system resources, then NTFS is required.
Note: Although DOS connot see NTFS, DOS applications running under NT can.
-- where C: is the drive letter to be converted from FAT to NTFS.
Converting FAT to NTFS preserves all data on the partition. This is a one-way process; there is no way to convert an NTFS partition to FAT.
If a process, including NT itself, is currently accessing the drive, an error message appears, stating the convert command cannot gain exclusive access the drive and connot convert now. Then this error message provides an option to schedule the drive for conversion when the system restarts.
You CANNOT convert an NTFS partitiion to FAT. To change NTFS to FAT, you must do:
Back up all files >> Reformat the partition with FAT, using format command or Disk Administrator >>Restore the files from the backup
NT automatically generates an 8.3 alias for each long file name (LFN) to allow Windows 3.x and DOS-based application to recognize and load LFN files.
LFN Entry 8.3 Entry 1 My Term Paper A.doc MYTERM~1.DOC 2 My Term Paper B.doc MYTERM~2.DOC 3 My Term Paper C.doc MYTERM~3.DOC 4 My Term Paper D.doc MYTERM~4.DOC 5 My Term Paper E.doc MY0F58~1.DOC 6 My Term Paper F.doc MY6968~1.DOC All file names characters that are not allowed in DOS are removed, such as spaces.
The conversion takes the first 6 characters of the LFN and uses a ~number to keep the name unique.
If there are already four files with the same first 6 characters, and the exact same 3 characters after the last period in the LFN, then the 5th keeps the first 2 characters of the LFN, but the next four random characters are generated by a hashing algorithm. For example, in above table, MY0F58~1.DOC. Only when the hashing of the middle four character (0F58) fails to generate a unique name, is the ~1 incremented to ~2.
For each LFN on FAT partitions, NT creates one folder entry for its alias and a hidden secondary folder entry for every 13 characters of the LFN. For example, the file name, This is a long Name.txt, is a 23 characters, and has three folder entries: one for the alias and two secondary for the LFN.
Folder entry for storing Alias Directory Entry THISIS~1.TXT Secondary Directory Entry 1 This is a Lon Secondary Directory Entry 2 g Name.txt
The FAT root folder has a hard-coded limit of 512 entries. If many LFN files are stored in the root folder, the user could run out of entries in the root folder; and the user would be unable to create any more LFN files, 8.3 files or folders in the root folder.
NT can be configured to prevent the use of LFN on FAT partiton (by modifying System Policy, or) by changing this registry value to 1: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\FileSystem\Win31FileSystem
On a FAT partition, a mixed-cased file name generates an uppercase alias, even if the original file name meets the 8.3 requirement. For example, MyFile.txt generates an alias of MYFILE.TXT on a FAT partition. However, this same file on an NTFS does NOT generate an alias.
NTFS system support automatic compression and decompression of files and folders. Compression can be performed on individual files, folders, and even entire drives.
Note: for performance reason, compression is NOT supported on NTFS partitions with cluster sizes greater than 4 KB.
On a NTFS partition, each file and folder has a compression attribute. Note that if the compression attribute is set for a folder, it indicates that any files created in that folder are automatically compressed.
NT Explorer -- check or clear the Compress check box when examine the attribute of a folder or a file. When you compress or decompress a folder, you will be prompted to indicate if you will also compress or decompress the subfolders; if not checked, action will be only on the files in the folder; subfolders retain their compress attribute state.
Compact.exe command
Note: Any user that has Read and Write permissions can do compressing and decompressing
If NT is installed on an NTFS partition, it is possible to compress the entire systemroot folder and subfolders. However, it is not possible to compress the NT Boot Loader (NTLDR) if you are booting from an NTFS partition on an Intel x86-based computer.
Pageing files cannot be compressed while in use. A closed paging file from another NT installation can be compressed, but when that installation restarts, the paging file is immediately decompressed.
Copying -- the file inherits both the compression attribute and permission of the target folder, regardless from which NTFS partition.
Moving -- if on the same NTFS partition, the file retains its own compress attribute and permission
-- if move to another NTFS partitiion, same as copying, the file inherits both the compression attribute and permission of the target folder (this is because a move between partitions is actually a copy-and-delete operation)
Only when moving on the same NTFS partition, the file/folder retains its own compress attribute and permissions.
FAT NTFS File name and folder length 255 characters 255 characters File size 4GB 4GB~64GB actual, 16EBtheoretical Partition size 4GB 2TB actual; 16EBtheoretical Attributes Read Only, Archive, System, Hidden Compress, and further extensible Accessible through many OS' NT only Built-in security No Yap Suports file or folder permissions /security No Yap automatic file and folder de-/ compression No Yap Transaction-based recoverability No Yap Support for Macintosh files (for support Services for Macintosh on NT Server) No Yap Support for POSIX requirements: case-sensitive naming, additional time stamp and hard links. No Yap Suitable for drives and partitions smaller than 400MB
low system overhead;-- larger than 400MB
-- high system overheadDisadvantage Can decrease performance if drives or partitions larger than 400MB Not efficient for volumes smaller than 400MB because disk overhead are 1-5MB
Only when moving on the same NTFS partition, the file/folder retains its own compress attribute and permissions. In all other cases, will inherits those of the target.
A hard disk can be divided into maximum of 4 partitions (primary + extended).
If there are four partitions, up to four can be primary (then no extended), but only one can be extended (3 primary + 1 extended).
NT supports several types of partitions -- primary and extended partitions, volume sets, and stripe sets.
Note: the difference between Partitions and Drives:
- one primary partition = one dirve (automatically);
one extended partition = one~many drives (you divide the extended partition into logical drives one by one manually) --- that's why should extended partition exist!
Primary partition -- can be marked as active and used by the system to start the computer. A primary partition cannot be divided into smaller partitions.
All partitions used by Win9x or MS-DOS must be formatted with the FAT file system.
On RISC-based computers, the primary partitions created by the manufacturer's configuration program must be FAT, and at least 2 MB in size.
Some OS, such as MS-DOS 5.0, can only recognize only one primary partition per disk, even if they are formated with FAT.
Extended partition -- an extended partition is a method for avoiding the four-partition limit, and for configure a hard disk into more than four logical volumes.
An extended partition is effectively a logical disk. Unlike a primary partition, you do not format the extended partiton, nor is it assigned a drive letter. Instead, you create one or more logical drives within it, and each logical drive is assigned a drive letter. You format each logical drive with a particular file system; this allows additional drive letters for organizing multiple file systems, applications, data files, and so on.
(Note: Primary partitions are assigned drive letters and formatted directly; Extended partitions must be devided into logical drivers at first, then format each logical driver. You cannot format the extended partition directly)
NT System and Boot Partitions -- NT system partition must be a primary partition. NT boot partition can be either a primary or a logical drive in an extended partition. (simply remember this wordings are the opposite to Windows9x and MS-DOS)
A volume set is a partition formed by collecting 2 to 32 areas of unformatted free space on one or more hard disks. Create a volume set when you have disk space from two or more unused areas that can be combined into a single large partition, or when an application requires a larger amount of disk space than you have on any single hard disk.
Each area is referred as a member of the volume set. When creating a volume set, the free space can be an unallocated are within an extended partition, or an unpartition area elsewhere on the disk.
A volume set can combine areas from different types of hard disks, including SCSI, ESDI and IDE.
Guidelines for Managing Volume Sets
- can store neither NT boot nor NT system partition
- cannot be accessed by Win 95, MS-DOS
- do not provide any fault tolerance. (In fact, volume sets spanning mutiple hard disks are more susceptible to failure because a failure on any of the hard disks will destroy the full volume set.)
- data is written to members one-after-one in a volume set
- cannot reclaim portions of disk space used without losing the entire volume set and all of the data stored on it.
Stripe sets are similiar to volume set in that they also combine areas of unformatted free areas into one larger logical drive. And stripe sets, like volume sets, can include disk space from as many as 32 hard disks and can combine areas on different hard disks, such as SCSI, ESDI, and IDE.
The amount of space used on each disk will be equal to the smallest unpartitioned space that you selected on the disks.
Guideline for Managing Stripe Sets
-- Similiar to volume sets in the following ways:
- Neither NT boot nor NT system partition can be reside in a stripe set.
- Win 95, MS-DOS cannot access info in a volume set.
- do not provide any fault tolerance, because there is no data redundancy. In fact, a stipe set spanning two or more hard disks are more susceptible to failure because a failure on any of the hard disks will destroy the full stripe set.
- cannot reclaim portions of disk space used without losing the entire volume set and all of the data stored on it.
--- Unlike a volume set:
- a stripe set requires at least two hard disks (a volume set can be implemented with a single hard disk).
- In a stripe set, data is written evenly across all of the physical disks, one row at a time. The NT implementation of stripe sets writes these in 64 KB units.
Stripe Set vs Volume Set
Condition Stripe Set Volume Set Manimum and Maximum areas can be combined 2~32 Can it contain the NT system or boot partition No Can be accessed by Win95 or DOS No Can use areas on different types of Hard Disk Yes Can it created on one hard disk? No (at least 2) Yes Can be extended after being created? No Yes (NTFS only) Must the areas combined of about same size? Yes No Sequence of data writing to areas one row at a time,
evenly across all the physical disksarea after area Can improve disk I/O performance? Yes No
Adding hard disks -- There is no need to indicate to NT that a new hard disk has been added. As long as the drivers are installed for the disk controller, NT automatically detects the hard disk and allows it to be partitioned and used.
Removable media --can have only one partition, and it must be primary partition. They cannot be part of a volume set or stripe set, and cannot contain an NT system or boot partition.
NT supports formatting removable media as either FAT or NTFS. However, if the removable disk is formatted as NTFS, the computer must be shut down and restarted to change disks. ?? a floppy is NOT a removable media, you cannot format a floppy as NTFS!
Can be thought as a graphical NT version of MS-DOS fdisk utility and the MS LAN Manager Fault Tolerance character applications, into one graphical interfac, for managing hard disks (no operations of floppy disks).
Disk Administrator cannot be used to further partition the system partition because it contains files required to operate Windows NT Server.
Partitioning the internal hard disk on a new computer is done during initial setup when you load the NT operating software.
- Making changes to that disk or partitioning an additional new hard disk is done using the Disk Administrator program.
The first time Disk Administrator run, or one or more disks have just been added, you will be prompt to write a 32-bit signature that identifies the disk (s). This signature is written in the Master Boot Record. Even if a disk if moved to a different controller, or its identification is changed, Disk Administrator and the NT fault tolerance (Ftdisk.sys) recognize it. (Note: fault tolerance is included ONLY in NT Server)
Writting a signature is a safe operation and will not affect ability to access this disk from other operating systems, such as DOS.
Note: You can open Disk Administrator only if you are logged on as a member of the Administrators group.
Use >>Disk Administrator >>Partition >>Create / Creat Extended ... to create a new partition
Use either of the 2 ways to format a partition:
- format d:/fs:FAT | NTFS
- >>Disk Administrator >>Tools >>Format
Partitions except the NT system and boot partitions and a partition containing an open file (i.e. Pagefile.sys) can be deleted at any time using Disk Administrator.
To remove the system and boot partitions --
- Booting from another operating system such as MS-DOS, and then deleting the partitions
- Booting from NT Setup Disk 1, then Disk 2, 3, as if doing an installation. Then choose to delete or create partitions.
Creating volume sets --
If you choose to use less than the total available space, Disk Administrator uses an equal percentage of the free space on each disk to create a partition of the size you specified. A single drive letter is assigned to the collection of partitions that make up the volume set.
Volume set can be formatted with either FAT or NTFS. However, only NTFS volume sets can be extended.
Operating systems, such as MS-DOS, that do not have volume-set functionality cannot recognize any volume sets that are created by NT. Therefore, if you create a volume set on a dual-boot computer, those partitions become unusable by MS-DOS or Win95.
The changes make will not be saved until you either click Commit Changes Now or quit Disk Administrator.
Extending volume sets
You can only extend a volume set that is formatted with NTFS. There is no way to extend a FAT volume set directly; you have to convert the volume to NTFS then extend it.
The changes you make will not be saved until you click Commit Changes Now or quit Disk Administrator.
After a volume set is extended and the configuration is saved, space cannot be reclaimed without deleting the entire volume set.
Existing NTFS volumes and volume sets can also be extended by adding free space. Disk Administrator forces the system to restart after you quit and save your changes, and then formats the new area without affecting any existing files on the original volume or volume set. However, once a volume set is extended, no portion of it can be deleted without deleting the entire volume set.
Deleting volume sets
Deleting a volume set deletes all info on all parts of the volume set and returns free space.
NT will not let you delete the volume with the system files. Nor can you delete individual partitions that are part of a set without deleting the entire set.
But, on a RISC-based computer, you can delete the system partition with the files needed to load Windows NT, so be very careful. NT also requires that all the logical drives or other volumes in an extended partition be deleted before you can delete the extended partition.
The changes you have made will not be saved until you click Commit Changes Now on the Partition menu or quit Disk Administrator.
Stripe sets CANNOT be extended
Stripe sets are created/deleted similarly to volume sets, but with more restrictions. Each member partition of the stripe set must be on a different disk up to a limit of 32 disks. Also, Disk Administrator will make all the partitions approximately the same size.
Disk Administrator divides the total size by the number of disks to create equal-sized unformatted partitions in each of the selected disks and assigns a single drive letter to the collection of partitions that make up the stripe set. If you choose a number that cannot be divided equally, Disk Administrator rounds to the closest higher or lower value.
Operating systems that do not have stripe-set functionality, such as MS-DOS, cannot recognize any stripe sets that are created by NT. If you create a stripe set on a dual-boot computer, those partitions become unusable by MS-DOS.
If you make changes and commit to them upon quitting, Disk Administrator makes the requested changes and displays a message when the disks have been successfully updated. Sometimes after you click OK, another message will advise you that changes have been made that require you to restart the computer. This happens when, for example, you extend a volume set, lock a volume, or search for or restore disk configuration information. When you click OK, Disk Administrator initiates a complete system shutdown, closes all open applications, and restarts the computer.
NT assigns partition numbers to all primary partitions before assigning partition numbers to any logical drives within an extended partition. (refer to the illustrations on page 226)
Important! -- If the NT boot partition resides on an extended partiton that was subsequently renumbered, then the Boot.ini file must be manually updated so that it point to the boot partitions.
Refer to the illustration on page 228.
- Starting with Disk 0, the first primary partition on each disk is assigned a consecutive drive letter, begining with the active system partition as drive C.
- Then, starting with Disk 0, logical drives on each disk are assigned the next consecutive letter(s).
- The remaining primary partition on each disk with assigned partitions are each assigned a letter.
In summary, drive letter sequence are assigned in this order/cycle: first primary partition on every HD -> logical drives ->remaining primary partitions
Note:
NT allows the static assignment of drive letters on volumes, partitions, and CD-ROM drives. This means that a drive letter (if not already in use) can be permanently assigned to a specific hard disk, partition or volume, or a CD-ROM drive. When a new hard disk is added to the computer, it will not affect statically assigned drive letters.
All drive letter modifications made with Disk Administrattor can be done without restarting the computer, if the selected partition does not contain NT system files.
Disk configuration info is initially stored on the Emergency Repair Disk (ERD) and in the systemroot\Repair folder at system installation. Every time when a changes is made to hard disk(s), Disk Administrator provides an option for saving the info and updating the ERD.
Restoring computer disk configuration info is useful when:
A new version of NT is being installed, and you want to restore current configuration
the computer was recently recovered with the Emergency Repair process and the registry was restored to its initial state (in case you didn't update the ERD), then you can restore the configuration use the info saved on the hard disk (in the \Repair folder?)
You can use the Repair Disk utility Rdisk.exe (in systemroot\System32 folder) to update the repair info, or to create a new Emergency Repair Disk using the repair info currently saved on your hard disk.
The repair information on your hard disk or your ERD can be used to reconstruct NT system files, system configuration, and startup environment variables if they become damaged.
The Repair Disk utility should not be used as a backup tool.
Failure to recognize hard disks or partitions -- If cannot recognize disk, incompatibility problem. If can recognize the disk but cannot access the partition, problem is in either partition table or the boot sector.
More serious problems: use a file system repair utility. If a logical driver appears corrupted and a backup exists, then reformat the drive and restore the files.
NT
can be configured to prevent the use of LFNs on
FAT partitions by changing this registry value to
1:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\FileSystem\Win31FileSystem
To overcome this limit, either the computer's BIOS must be able to circumvent the limit, or NT must be able to communicate directly with controller.
Fault tolerance is designed to combat problems with disk failures, power outages, or corrupted operating systems. Fully fault-tolerant system include redundant disk controllers, power supplies, and UPSs.
Always remember that fault-tolerant system should never be used as a replacement for the regular backup of servers and local hard disks. A carefully planned backup strategy is the BEST insurance for recovering lost of damaged data.
RAID (Redundant Arrays of Inexpensive Disks) provides fault tolerance by implementing data redundancy -- data is written to more than one disk in a manner that allows recovery of the data in the event of a single hard disk failure. RAID technology is standardized and categorized in levels. NT supports two software implementation of RAID:
RAID 1 -- mirror set, and RAID 5 -- stripe set with parity.
Hardware and Software Implementation of RAID
RAID fault tolerance can be implemented as either a hardware or software solution. Consider the following points when deciding whether to implement fault tolerance in hardware or software:
- Fault-tolerant software is available only on NT Server. NT Workstation does not provide fault tolerance.
- System performance is usually faster with hardware fault tolerance.
- A hardware fault tolerance solution may lock you into a single hardware vendor.
- In a hardware fault tolerance implementation, some hardware vendors allow replacement of a failed drive without shutting down the system.
- Hardware implementations of RAID, some of them are vendor-specific and bypass the fault tolerance of the software drivers of the operating system, usually offers performance improvements over software implementations.
Note:
- Implementing fault tolerance, regardless of using hardware or software, does not reduce the need for regular backup.
- Following a failure, there is no fault tolerance until the fault is repaired. If a second fault occurs before the data lost from the first fault is regenerated, you cannot recover the data without restoring it from a backup.
- NT Server supports two software fault tolerance methods -- RAID 1 and RAID 5
RAID 1:Mirror Sets
Mirror sets use the NT fault tolerance driver (Ftdisk.sys -- Fault tolerance ) to simultaneouly write the same data to two physical drives.
Hardware Requirements for a Mirror Set -- one controller, two (drives on different) physical disks
Note: NT Server configure fault tolerance at level of logical drive letter, not the physical disk level. The two members of a mirror set have the same driver letter. (but the two member must on two different physical hard disks controlled by the same disk controller!).
Features of RAID 1:
any partition, including NT system and boot partition, can be mirrored, i.e. ONLY mirror set and disk duplexing can protect the NT system/root partition with fault tolerance.
Mirror set without disk duplexing CAN NOT protect against controller failure.
provides enhanced READ performance, because the fault tolerance driver can read from both members at the same time.
slight decrase in WRITE performance, because the fault tolerance driver must write to both members simultaneously.
higher cost per megabytes, because disk utilization is only 50%. However, for peer-to-peer and small server-based LANs, mirror sets usually have a lower initial cost because it requires only two disks.
Disk Duplexing -- each physical disk in the mirror set has its own controller. In this way, the mirror set is protected against both controller failure and disk failure.
Without disk duplexing, i.e. both physical disks that comprise a mirror set are controlled by the same disk controller, then when the disk controller fails, both members of the mirror set are inaccessible.
Disk duplexing also reduces bus traffic and potentially improve READ performance.
Hardware Requirements for a Disk Duplexing -- TWO controllers, two (drives on different) physical disks
Disk duplexing is a hardware enhancement to NT Server mirror set. No additional software configuration is necessary.
RAID 5: Stripe Sets with Parity
Parity is a mathematical method of verifying data integrity. Fault tolerance is achieved by adding a parity-info stripe to EACH disk partition in the volume.
RAID 1 vs RAID 5
| RAID 1 -- Mirror Sets | RAID 5 -- Stripe Sets with Parity |
| Supports/Can be implemented on both FAT and NTFS | |
| Can mirror system or boot partiton | Can NOT mirror system or boot partiton |
| Uses 2 and only 2 hard disks | Requires minimu 3, maximum 32 hard disks(same as Stripe Set) |
| Improved read performance | Better read perf. than RAID 1, especially with multiple controllers |
| Slightly decreased write performance. | Slower write perf (due to parity calculation) |
| Use less system memory | Use more system mem for parity calculation |
| Can Win95/MS-DOS access? should | Can Win95/MS-DOS access? No |
| Higher cost per MB (50% utilization) | Lower cost per MB (overhead = 1/n, n is the the number of HD's in use) |
RAID 1 (mirror set) and 5 (stripe set with parity) can coexist on the same computer.
Because a stripe set with parity cannot include the system or boot partition, consider protect the system and boot partitions in RAID 1, and protecting the remaining data in RAID 5.
When implementing RAID 5, same as when using stripe sets --
The free spaces that are combined to create a stripe set with parity should be the same size. If not, Disk Administrator makes each partition of the set approximately the same size and leaves the unused portitions of the partitions as usuable free space.
- Deleting a mirror set with parity deletes all of the info stored in that volume.
When a member of a mirror set or a stripe set with parity fails, the fault tolerance driver directs all I/O to the remaining member(s). This ensures continuous service.
You can configure the computer to send administrative alerts (use Server Manager) to notify the specified accounts that this failure has occured.
Note: if the failed disk is part of a mirror set that contains the boot partition, and if the failed disk is the primary physical drive, then a fault tolerance boot disk will be required to restart the system.
When either member of mirror set fails, the system continues to function.
However, if it is a mirror set for boot or system partition and the primary member failed, you will need to use the fault tolerance boot dik, and modify the ARC path in the Boot.ini to change the operating system entry to point the mirrored copy of the boot partition.
Steps to recover a mirror set:
- Break the mirror set (using Disk Administrator -->Fault Tolerance >>Break Mirror) first, in order to replace the failed member.
Note: Regardless of which disk contains the fault, when the mirror set is broken using the Disk Administrator command, the secondary/mirrored member is assigned the next available drive letter of the computer. Therefore,
If the failed drive is the primary member, assign the drive letter that was for the complete mirror set to the working member, i.e. the secondary/mirrored member.
Delete the failed partition.
Using free space on another disk, create a new mirror set relationship.
Note: Use Event Viewer to look at the System Log to determine which partition/member failed.
If a member of a stripe set with parity fails, the computer continues to operate and to gain access to all data, however, with decreased system preference, because the fault tolerance driver needs to use the parity bits to regenerate the missing data in RAM.
To regenerate the data and return the computer to it previous performance level, use >>Disk Adminstrator >>Fault Tolerance >>Regenerate
When making a mirror set for the boot or system partition, it is important to create a fault tolerance boot dik for use in case of physical disk failure. (Remeber only mirror sets can provide fault tolerance for the boot and system partitions). Steps to make a fault tolerance boot disk:
Format a disk using NT Server (a Fault Tolerance Boot Disk must be formatted on NT Server! remember there is NO fault tolerance in NT Workstation)
- Copy the following files from the primary partition of the NT Server computer (x86-based) :
Ntldr, Ntdetect.com, Boot.ini, and if exist-- Ntbootdd.sys (for SCSI disks not using SCSI BIOS or is disenabled), and Bootsect.dos (if it's dual boot)For RISC-based computer: Osloader.exe, Hal.dll, and *.pal
Edit Boot.ini to change the operating system entry (ARC paths) to point to the mirrored copy of the boot partiton
why the file is named BOOT.ini
- ARC is used to tell where is your NT operating system
the NT operating system, i.e. the \winnt\system32... folders, is on the BOOT partition
Test the boot disk to ensure it works and boots using data from the mirrored copy of the boot partition.
Creating a fault tolerance boot disk for recovery of a mirrored boot or system partition requires editing the ARC (Advenced RISC Computing) names in the Boot.ini file.
[boot loader] timeout=18 default=multi(0)disk(0)rdisk(0)partition(1)\WINNT [operating systems] multi(0)disk(0)rdisk(0)partition(1)\WINNT="Windows NT Server Version 4.00" multi(0)disk(0)rdisk(0)partition(1)\WINNT="Windows NT Server Version 4.00 [VGA mode]" /basevideo /sosAs in the Boot.ini file above, the ARC path points to location (s) of the operating system files. Two ARC Formats are multi and SCSI naming:
multi(x)disk(y)rdisk(z)partition(a)
scsi (x)disk(y)rdisk(z)partition(a)
Convention Description multi /scsi scsi... indicates a SCSI controller on which SCSI BIOS is not enabled (i.e. when file Ntbootdd.sys exists). Remember, use scsi only when Ntbootdd.sys exists. multi represents all other adapter or disk controllers, including SCSI with BIOS enabled so that the SCSI disk is accessed by the SCSI BIOS.
(x) Ordinal number, starting from 0, of the hardware adapter. disk(y) SCSI bus number. For multi, this value is always 0 rdisk(z) Ordinal number of the disk. For scsi, this value is always 0 (ignored actually) partition (a) Ordinal number of the partition starting with 1.
Note: all non-extended partitions are assigned numbers first, followed by all logical drives in extended partitions.Example1: (refer to the illustration on page 255)
A NT Server computer has two adapters -- one multi adapter, controlls 2 hard disks: the 1st HD has two partitions -- drive letter C: and F: the 2nd HD also has two partitions -- driver letter D: G:
The scsi adapter, 1 HD, has 1 partition, driver letter -- E:
When Boot Partition is located on ARC Path is drive C: drive G: drive E:
Note: ARC path uses ordinal numbers for partitions on each HD. Don't mix them up with the Drive Letters of the system!
NT is designed to run applications written for existing OS' such as MS-DOS, OS/2, Win3.x. It achieves this through environment subsystems, which emulate different os environments.
NT uses two processor modes -- user mode and kernel mode, to maintain operating efficiency.
Less privileged processor mode than kernel mode, and has no direct access to hardware. Code running in user mode are only in its own address space. It uses well-defined os APIs to request system services. Applcations, and the subsystems that support them, run in user mode.
Have no direct access to hardware. Hardware access requests must be granted by kernel mode component.
Are limited to an assigned space. NT helps protects the os by limiting the areas of memory that a user mode process can access. This limitation is accomplished by assigning only certain addresses to the user mode process.
Can be pagged out of physical memory into virtual RAM on a hard disk. In this manner, the user mode processes have access to more memory than is actually available to them.
Process at a lower priority than kernel mode compenents. This ensures that os does not slow down or have to wait while an application finishes processing.
Process -- when an application is started, a NT process is created. A process is implemented as an object. An object consists of an executable program, a set of virtual memory addresses, and one or more threads.
Threads -- are objects within processes that run program instructions. They allow concurrent operations within a process and enable one process to run different parts of its program on different processors simultaneously.
Object -- any piece of info, created by using Windows-based application, that can be embedded or linked into another document.
Subsystem Overview
NT supports applications by using environment subsystems, which provide API services to applications written for a specific environment or operating system. An environment subsystem in NT is an intermediary between an application and the Executive Services. The environment subsystem translates the instructions from the application into instructions that the Executive Services can carry out.
There are 4 subsystems -- POSIX, Win32, OS/2 and Security subsystems. Among them:
the POSIX and OS/2 subsystems are designed for supporting other operating environment than NT.
- Security subsystem supports the logon process only. It does not support other applciations.
Common operating system functions are implemented once in the Executive Services, rather than duplicated in each subsystems. This reduces the effort required to develop new subsystems and make them easier to maintain.
In NT 4.0 (different from NT 3.x), the Win32K Window Manager and GDI are incorporated into the Executive Services. Having Window Manager and GDI run in kernel mode enhances system performance. (Win32K Window Manager and GDI are responsible for handling all GUI-related I/O requests, maintaining dispaly, and providing a common GUI for all applications)
-- the privileged mode of operation in which the code has direct access to all hardware and all memory, including the address spaces of all user mode processes.
Can access hardware directly
Can access all of the memory on the computer
Are not moved to the virtual memory page file on the hard disk (Kernel mode processes DO NOT use virtual RAM themselve)
Process at a high priority than user mode processes.
Comprised of NT Executive, which includes three layered components that run in kernel mode -- the Executive Services, the microkernel, and the hardware abstration layer (HAL).
Executive Services -- central to all major os functions. It has two services:
- Managers -- various modules that manage I/O, objects, security, processes, interprocess communication, virtual memory, and window and graphical management.
- Device drivers -- software components than control hardware access.
Microkernel -- provides most basic os services, such as thread scheduling, first-level interrupt handling, and deferred procedure calls. It resides between the Executive Services and HAL layers.
Hardware Abstraction Layer -- a library of hardware-manipulating routines provided by MS or by the hardware manufacturer. HAL hides the characteristics of the platform behind standard entry points so that all platforms and architectures look alike to the operating system. It enables the same operating system to run on different platforms with different processors.
The memory architecture of NT is a demand-paged, virtual memory system. It is based on a flat, linear 32-bit address space, which allows each process in NT have access to up to 4GB of memory, in other words, NT can provide up to 4GB memory space for each application.
Virtual Memory -- with virtual memory, all applications seem to have a full range of memory addresses available. NT does this by giving each application a private memory range called a virtual memory space and by mapping that virtual memory to physical memory. Each virtual memory space has room for 4GB of addresses. This address space is made up of 1MB (1,048,567) of 4KB pages ( NT maps physical and virtual memory addresses in 4KB blocks called pages).
Virtual RAM allows hard disk space to be used as if it were additional memory. In this manner, the user mode processes have access to more memory than is actually available on the system.
Note: kernel mode processes /applications run ONLY in physical RAM. Or, ONLY user mode applications can be paged to the virtual RAM.
Virtual Memory Process-- this process makes use of the paging file(s), or in other name swap file, on the hard disk (pagefile.sys). The process of managing which pages are stored in RAM, and which are stored in the paging file, is called demand paging.
Task Manger is used to monitor and prioritize applications and processes, and to view system performance data.
To change the priority of a running applicaiton ->>Task Manager >>Processes >>right-click the application >>Set Priority
To assign a Process to a Processor (on multiprocessor computers) ->>Task Manager >>Processes >>right-click the application >>Set Affinity (visible only to multiprocessor computer!)
Multithreaded applications -- Win32-based applications can simultaneously execute multithreads, or execution units of a process.
Reliability -- Each Win32-based application runs in its own 2GB address space. For this reason, a Win32-based application cannot corrupt the memory of another, or, when it fails it does affect, other Win32-based applications.
NT supports these interfaces that are used in Win32-based applications:
MS-DOS-based applications run in a special Win32-based application called an NT Virtual DOS Machine (NTVDM), which provides a simulated MS-DOS enrironment.
Each MS-DOS application has it own NTVDM, and each has a single thread. Each NTVDM is independently supported in its own address space, so that if an failed NTVDM will not affect all other NTVDMs.
A NTVDM comprises of Ntvdm.exe, Ntio.sys (equivalent of MS-DOS Io.sys), Ntdos.sys (equivalent of MS-DOS Msdos.sys), and Virtual Device Drivers (VDDs) -- to allow DOS applications to access the system hardware (Remeber, DOS applications attempt to access hardware directly, while in NT applications that run in user mode can not directly access hardware).
An NTVDM can be customized for a specific MS-DOS application by changing setting in the application's PIF (program info file), which is in fact the same as the properities of the shortcut to that MS-DOS application.
To create, modify, and save PIFs (automatically) ->>NT Explorer >>right-click the application file name >>Properties >>OK ... The PIF (shortcut) for that application is created.
Autoexec and Config NT file names
Note: the Autoexec.nt and Config.nt are used only for backward compatibility for DOS programs
In NT, PIFs have the Autoexec filename setting and the Config filename setting (such settings are NOT available in Win3.x PIF). This character allows you to specify a different Autoexec and Config files for any specific DOS application.
The default file names are Autoexec.nt and Config.nt, in systemroot\System32 folder.
To specify different Autoexec and Config files -->> right-click the DOS application PIF (shortcut) >>Program >>Windows NT... >> type in the Autoexec filename and Config filename
Note:
NT supports the same commands in the Autoexec file that are supported in MS-DOS 5.0.
Although most DOS applcations can work under NT, any DOS dervers or executable files that attempt to directly access a device for which there is no VDD will fail. NT protects the system from such access.
PIFs are for MS-DOS applications only, Windows 3.x, OS/2, and POSIX based applications do not use PIFs.
When you use the Run command on the Start menu to start an MS-DOS-based application, NT searches for a PIF to use with the MS-DOS-based application:
- If it finds one, NT starts the application using the PIF
- If no PIF is available, NT uses _Default.pif
WOW (Win16 on Win32) is a 32-bit user-mode program in NT that allows Win16 applications to run in a Win32 environment.
Win16 applications are primarily designed to run in Win3.x, which is itself an MS-DOS-based program, therefore Win16 applications require an NTVDM and WOW (operates in the context of this NTVDM).
WOW environment consist of several components -- Wowexec.exe, Wow32.dll, krnl386.exe, User.exe, Gdi.exe, and the Win16 applicaiton running in the WOW.
WOW thunks, or translates, 16-bit calls to 32-bit calls. Thunking is the process of translating 16-bit calls into 32-bit calls and vice versa.
WOW provides nonpreemptive multiprocessing (or cooperative multiprocessing) environment for which Win16-based application were designed. By default, a single NTVDM starts when the first Win16 application is initialized, and all Win16-based applicaitons run in that same NTVDM and WOW. Thus,
WOW has these limitations:
- if one Win16 application fails, it can adversely affect all other Win16 applications running in the same NTVDM.
For example, if a Win16 application does not release the processor, the other Win16 applications cannnot get access to it, because WOW provides nonpreemptive multiprocessing within that environment. In order for the other Win16 applications running in that NTVDM to gain access to the processor, the failed Win16 application must be closed.
Note: only the Win16 application running in that NTVDM are affected, all other programs are NOT affected.
- There is no shared memory between the application running in WOW and other applications (Non-Win16 app.?) running under NT.
Note:
- Win16 applications cannot call 32-bit DLLs, and NT-based applications cannot call Win 16 DLLs either!
- 16-bit Windows 3.x VDDs (virtual device drivers) are NOT supported under WOW. If a Win16 application rely on these drivers, it may not function corrctly under NT.
Multiple NTVDMs for WOW -- to resolve the above-mentioned limitations of a default single NTVDM of for WOW
Win16-based applcations can be configured to run in their own memory spaces, on an application-by-applcation basis, thereby creating multiple NTVDMs.
If a Win16 application is configured to run in its own memory space, a new NTVDM is created when it starts, and a new WOW application environment within that NTVDM.
Advantages of Multiple NTVDMs, i.e. running Win16 applications in separate NTVDMs (memory spaces) -- if compare to default single NTVDM for all Win16 applications
Reliability -- a single faulty Win16 application does not affect any other Win16 applications.
Interoperability -- if Win16 applications follow the OLE and DDE (dynamic data exchange) specifications, they can interoperate with other applications in separate memory spaces.
Remember: There is no shared memory between the application running in WOW and other applications running under NT.
Preemptive multitasking -- because each application runs in its own memory space, a busy application will NOT prevent other application to use memory, as would happen in the default single NTVDM.
Multiprocessing -- can take advantage of multiprocessor computers. All the Win16 applications can run simultaneously.
Disadvantages of Mutiple NTVDMs for Win16 applications
Additional memory usage
Lack of interoperability -- If Win16 applications do not follow the OLE and DDE standards, or if they rely on shared memory to exchange data, these Win16 applications do not function correctly in separate memory spaces. To function properly, such applications must be run in the default (shared) NTVDM and WOW application environment.
Starting a Win16 Application in its own NTVDM -- /separate
A Win16 application can be started in its own NTVDM in any of the following ways:
>>Command Prompt >> Start /separate executable_path_and_name
>>Start >>Run >>Open executable_path_and_name, check Run in Separate Memory Space check box (if this check box appears dimmed, either this application is not 16-bit, or the file cannot be found)
From a shortcut >>Properties >>check Run in Separate Memory Space check box. If you want to configure a Win16 application always start in a separate NTVDM, create a shortcut for the application.
NT Explorer >>View >>Options >>File Types >>click the Win16 application >>Edit >>edit the open line to include the /separate switch:
cmd /c start /separate <path><application_name>Note: Once started, the default (shared) NTDVM and WOW application environment remains open, even if all Win16 applications that were running in it were closed. (use Task Manager to close the shared NTDVM and WOW).
When a Win16 application is started in a separate memory space, an additional NTVDM and WOW is started. When you close this Win16 app., it NTDVM and WOW is also closed. However, the default NTVDM is not affected, as always.
| Hardware Platform |
Win32 Applications |
POSIX Application |
Win 3.x, DOS Applications |
OS/2 Applications |
| Intel x86 | Source-compatible |
Binary-compatible |
||
| RISC | ||||
Source-compatible application -- must be recompiled for each hardware platform, i.e. software in one platform cannot be used in the other platform without recompilation.
Note: NT supports 16-bit character-based OS/2 applications (version 1.3 only) on x86-based computers only. OS/2 bound applications (applications that can run under both OS/2 and MS-DOS) run on RISC-based computers using the MS-DOS subsystem.
NT supports only OS/2 1.3; it does not support OS/2 higher versions.
to enable some graphical capabilities for OS/2, install an additional NT component Presentation Manager
Interoperability --
All NT-based applications can share data using the NT Clipboard <ClipBook Server service permits cutting and pasting over the network >
Windows 3.x-based (Win16-bit??) and Win32-based applications can share data using OLE and DDE.
POSIX is a standard for versions of UNIX and UNIX-like operating systems.
NTFS is the only POSIX.1-compatible file system.
Distribute Component Object Model (DCOM) uses remote procedure calls (RPCs) and NT security features, such as permissions, to enable application to communicate across networks. One example of an application requiring DCOM would be a stock quote service.
DCOM is network OLE -- that is, COM with a longer wire. It uses the same tools and technologies as COM.
DCOM has its roots in Microsoft's object technology, which has evolved over the last decade from DDE (Dynamic Data Exchange, a form of messaging between Windows programs), OLE (Object Linking and Embedding, embedding visual links between programs within an application), COM (the Component Object Model, used as the basis for all object binding), and ActiveX (COM enabled for the Internet).
RPC provides the basis of communication and interoperability between the various DCOM services. RPCs allow an application to carry out procedures on a remote computer. DCOM uses an RPC to enable existing application to interact across multiple computers in a network.
Before you can use an application with DCOM, you must use DCOM Configuration to set application properties, such as security and location. Note:
On the computer running the client application (the application that initiates a request to a server application), you must specify the location of the server application (the application that responds to requests from a client application) that will be accessed or started.
- For the server application, you must specify the user account that will have permission to access or start the application, and the user accounts that will be used to run the application.
To configure DCOM:
>>Command prompt (or >>Start >>Run) >>dcomcnfg
For additional info on DCOM, see Appendix E- The Distributed Component Object Model
NT Command Prompt (Cmd.exe) starts a 32-bit character mode interface to NT and all of its subsystems.
Note: Starting the Command Prompt does not start an NTVDM. An NTVDM only starts when an MS-DOS-based application is launched.
Command Prompt can be used to:
- Start applications, incl. NT (32-bit), Windows 3.x (16-bit), MS-DOS, OS/2 1.x character-based, or POSIX applications.
- Start any batch file with the extension .bat or .cmd
- Issue any NT command
- Administrate or use network resources
- Cut and paste info between applications, incl. applications running in different subsystems.
- Mix commads from the different subsystems (e.g. pipe between an MS-DOS and a POSIX application)
Configuring the Command Promp
- Configuring the default settings for any instance of Command Prompt that the logged-on user runs.
>>Control Panel >>Console
Each user can configure default settings for the Command Prompt. The settings are stored on a user-by-user basis in this registry entry:
\HKEY_CURRENT_USER\Console
- Configuring Individual Command Prompts
To configure a Command Prompt that is currently running, in the upper-left corner of the Cmd.exe window >>click MS-DOS icon >>Properties, to configure in one of the two ways:
- Apply properties to the current window only
- Modify the shortcut which started this window
Priority levels range from 0 to 31. The base priority in normal (8). Critical system applications use higher priorities; others can use lower levels.
Priority Used by 0-15 Dynamic applications: User application and most system function that are not crucial to the performance of the system and can be written to the page file. 16-31 Real-time applications, such as the kernel, that cannot be written to the page file.
Running applications at a specified priority
In a preemptive, multitasking operating system such as NT, the microkernel schedules threads for the processor in order of their priority and interrupts running threads if a higher priority thread is ready to run.
- To start an application and change its base priority -->use Start command and one of these options:
option sets base priority to /realtime 24 /high 13 /normal 8 /low 4 For example, to start notepad.exe at low priority -->> Start /low notepad
- To change the base priority class after an application that has started:
Ctrl+Alt+Del >>Task Manager >>Processes >>right-click a process>>Set PriorityNote: Only users with Administrator privileges can use the /realtime option.
- To changing Foreground Application Responsiveness -- relative priority of foreground and background applications
>>Control Panel >>System >>Performance >>move the slid in the Boost settings of "Application Performance"
None -- the foreground applicaiton priority is not changed. All foreground and background applications retain base priority levels. Use this setting when all applications are equally important to the current task.
Middle -- the foreground applicaiton priority increases by one level; backgrouond applications maintain base priority levels.
Maximum -- the foreground applicaiton priority increases by two levels; backgrouond applications maintain base priority levels. Use this setting to run an important application the must receive as much CPU time as possible, but still allow background applications to have minimal access to system resources.
Note: priorities changed in this way are relative, that is, if a foreground applicaiton priority is changed, background applications' priority are changed correspondingly.
For a computer to access a NT, the client software must be installed and configured on that computer. On NT Server, NT Workstation, Win9x, the client software is automatically installed during installation of the operating system. For other operating system, such as MS-DOS, that does not include the networking components required to access NT, MS provides networking client software on the NT Server 4.0 compact disc. Such as:
· Microsoft Network Client version 3.0 for MS-DOS
· Microsoft LAN Manager version 2.2c for MS-DOS clients
· Microsoft LAN Manager version 2.2c for MS OS/2 clients
· Microsoft Remote Access Service client version 1.1 for MS-DOS
· Microsoft TCP/IP-32 for Windows for Workgroups version 3.11
· Microsoft Windows for Workgroups version 3.11
· Microsoft Windows 95 operating systemNote: NT Server 4.0 also supports WfW as a client, but does not include the WfW software. Because the version of TCP/IP included with WfW does not support DHCP and WINS, NT Server provides an add-on product, TCP/IP-32 for WfW 3.11, which supports DHCP and WINS.
You can use Network Client Administrator to do the following:
- Share the installation files contained on the Windows NT Server CD.
- Copy the directories and files contained on the CD to a network server's harddisk (recommended).
The software installation files are in the CLIENTS Directory of NT Server Setup CD. If you choose "Make Network Installation Disk Set" >>Copy Files to a New Directory, and then Share ... All files in the CLIENTS Directory of NT Server Setup CD are copied to the NT server, and shared. To save hard disk space, delete any folders that are not needed from the Clients folder.
Using the Network Client Administrator, you can quickly install network client software by creating a network installation startup disk or an installation disk set.
The type of installation disk you need to create depends on the type of software you intend to install. To determine whether you need to create a network installation startup disk or an installation disk set, see the Help topic "Determining the Type of Disk You Need to Create."
After you have installed the network client software on the target computer, you can install RAS for MS-DOS, TCP/IP-32 for WfW, or client-based network administration tools.
With Network Client Administrator, you do perform the four tasks:
-- Select this option if you want to create an installation startup disk that enables you to automate the installation process. During the installation process, the disk you create automatically: starts the computer, connects to the server containing the installation files, and initiates the installation process.
You can create network installation startup disks for the following network operating systems and clients:
· NT Server 3.5, 3.51, and 4.0
· NT Workstation 3.5, 3.51, and 4.0
· Windows 95
· WfW 3.11
· Network Client for MS-DOS 3.0
-- The disk set contains all the files needed to install network client software. You can create an installation disk set containing the actual installation files for:
· Network Client version 3.0 for MS-DOS
· LAN Manager version 2.2c for MS-DOS clients
· LAN Manager version 2.2c for MS OS/2 clients
· Remote Access Service client version 1.1 for MS-DOS
· TCP/IP-32 for Windows for Workgroups version 3.11Note: the installation disk set can be used only for the specific client or service you selected. If you have multiple computers with different client(s) or service requirements, you must make separate installation disk sets for each network client or service.
-- to any NT Workstation or NT Server computer for which you have administrative permissions. Clients (NT Workstation or Win9x) can then install the tools by connecting to the server. In Network Client Administrator, use the Copy Client-based Network Administration Tools option to:
To share the installation files for the client-based network administration tools on the NT Server CD.
To copy the installation files for the client-based network administration tools to a new directory on a network-server hard disk, and then share the files.
NT Server includes Client-based Network Administration Tools to use on NT Workstation and Windows 95 clients. These tools enable you to administer NT Server, LAN Manager for MS OS/2, or LAN Manager for UNIX from a Windows-based computer.
-- Remoteboot is a NT service that is used to start MS-DOS, Win3.x, and Win95-based computers over the network. The Remoteboot Service is installed through >>Control Panel >>Network >>Services
Note: you must install DLC protocol before install Remoteboot service
To start Network Client Administrator
-->>Start >>Programs >>Network Administrative Tools >>Network Client Administrator.
NT Server includes Client-based Network Administration Tools to use on NT Workstation and Win 95 clients. These tools enable you to administer NT Server, LAN Manager for MS OS/2, or LAN Manager for UNIX from a Windows-based computer. You have greater control when using a NT Workstation client because more of these tools are available for NT Workstation clients than for Windows 95 clients.
To use any of the Client-based Network Administration Tools, you must be a member of the Administrators local group at the computer you administer.
In Network Client Administrator, use the Copy Client-based Network Administration Tools option to:
- Share a folder that contains the Client-based Network Administration Tools.
The folder can either be on the hard drive of an NT Workstation or NT Server computer or on the Windows NT Server compact disc.
- Copy the Client-based Network Administration Tools to a new folder, and then share the files.
After you copy and share the Client-based Network Administration Tools, clients can install them by connecting to the share.
You can install the following Client-based Network Administration Tools on an NT computer Workstation:
- DHCP Manager
- Remote Access Administrator
- Remoteboot Manager
- Server Manager
- Services for Macintosh Manager
- User Manager for Domains
- WINS Manager
- User Profile Editor
You can install the following Client-based Network Administration Tools on a computer running Windows 95:
- Event Viewer
- Server Manager
- User Manager for Domains
In addition, when you install these tools, extensions are added to Explorer and My Computer to allow you to change security on NTFS drives, manage NT printers, and manage NT Servers running FPNW. <and to create new shares??>
Benefits of Services for Macintosh
NT Server Services for Macintosh (SFM) is a thoroughly integrated component of Microsoft Windows NT Server that makes it possible for PC and Apple Macintosh clients to share files and printers.
With SFM, Macintoshes need only the Macintosh operating system software to function as clients; no additional software is required. You can, however, set up the optional user authentication module, which is software that provides a secure logon to the NT Server.
After SFM is set up, an NT computer Server can also function as an AppleTalk router. Routing capability is supported for AppleTalk Phase 2.
After installing Services for Macintosh on a Windows NT Server computer, you can use the MacFile option in Control Panel or the MacFile menu in Server Manager to configure the Services for Macintosh server. You can also use the MacFile menu in File Manager or Server Manager to configure Macintosh-accessible volumes.
In summary, file sharing, printer sharing (and spooling for Macintosh users), Simplified administration, and AppleTalk routing
· File sharing -- For many applications that have versions for PCs and for Macintoshes, users of both versions can work on the same data file using SFM. When Macintosh users view directories on the server containing these data files, they see the files represented by the appropriate icon (Macintosh-style).
Even though the MS-DOS, OS/2, and Windows NT file systems differ greatly from that of the Macintosh operating system, both PC clients and Macintosh clients can use the same files stored on the server. SFM works in the background to make this possible.
For example, some people in your department use Microsoft Excel for Windows. Others prefer using Microsoft Excel for Macintosh. With SFM, these users can work on the same spreadsheet files.
· Printer sharing -- Clients can send print jobs to either a printer for PCs or a Macintosh-based printer. With SFM, all users can send print jobs to all printers. Moreover, you can control all of the print queues from a single location your NT computer Server or Windows NT Workstation.
SFM provides additional benefits for Macintosh users who use AppleTalk printers -- it provides spooling. With spooling, Macintosh users can start other tasks as soon as they send a print job to the NT Server, where print jobs are stored until a printer becomes available. Without spooling, users must wait until the print job completes before doing anything else.
· Simplified administration -- For example, you have several Macintoshes that you’d like to put on the network. With SFM, you don’t need a Macintosh server: Your NT computer Server can provide file sharing and file security for your Macintoshes and PCs.
By using your NT Server computer with Macintosh clients, you have only one list of users to maintain instead of two (one on a NT Server and one on a Macintosh server).
It also ensures a consistent file-level security for PC and Macintosh users. SFM translates file permissions, which adds a level of security to your network. SFM translates Windows NT file permissions and Macintosh-style permissions (referred to as access privileges by Macintosh users). The reverse is also true: Macintosh-style permissions are translated to Windows NT permissions for PC users .
Note: Both Administrators and Server Operators can administer SFM.
· AppleTalk routing support -- For example, suppose you want to connect an AppleTalk internet (a group of two or more AppleTalk physical networks). With SFM, you can attach networks with Macintosh clients to create an AppleTalk internet.
Services for Macintosh Requirements
- Requirements for Computers Running Windows NT Server
- 2 MB extra hard disk space
- A NTFS partition to create directories (Macintosh-accessible volumes) that can be used by Macintosh clients
- Requirements for Macintosh Clients
Version 6.0.7 or later (including System 7™ or higher) Macintosh OS, and AppleShare (the Apple networking software for the Macintosh). These include all Macintoshes except the Macintosh XL and Macintosh 128K.
In addition, SFM supports version 6.x or later of the LaserWriter printer driver, and the AppleTalk Filing Protocol version 2.0 and 2.1.
Volume size limitations of Macintosh client:
- · For Macintosh clients older than version 7.5, the volume size must not exceed 2 GB.
- · For version 7.5 or later Macintosh clients, the volume size must not exceed 4 GB.
Note: SFM supports LocalTalk, ethernet, token ring, and FDDI. Ethernet and token ring are commonly used when integrating Macintoshes into PC networks.
SFM can be installed during or after NT Server installation -->>Control Panel >>Services >>Add >>Services for Macintosh
If you remove SFM and later decide to set it up again, you must use the Windows NT Server distribution disk and installation program to copy the required SFM files to the server. Removing SFM deletes the distribution files (except Macintosh-accessible volumes) instead of disabling them.
Note You must be an administrator or have administrator permissions to use the Network icon in Control Panel.
-- Creating a Macintosh-Accessible Volume
A Macintosh user shares a file with PC users by storing that file in a Macintosh-accessible volume on the NT Server. After SFM setup, a MacFile menu (in Server Manager) is added for creating Macintosh-accessible volumes. Similar to creating a share (shared directory) for PC users, you can designate a directory as a Macintosh-accessible volume.
To create a Macintosh-accessible volume -->>File Manager >>select the directory that you want to designate as a Macintosh-accessible volume >>MacFile >>Create Volume
All Macintosh-accessible volumes must be created on an NTFS partition or on a CDFS volume. If you specify a CDFS volume, the Macintosh-accessible volume will provide read-only access. (In this case, CDFS volume refers to a hard disk volume.)
Note: If the directory is to be accessed by PC clients as well as Macintosh clients, make sure you share the directory using the Share As command on the Disk menu and designate it as a Macintosh-accessible volume.
Note: Machintosh computers have a maximum partition size of 2GB. If Macintosh clients access a NT Server with an NTFS partitions of more than 2GB (for version <7.5; from 7.5, partition limitation is 4GB), the clients may get a message that there are 0 bytes available.
When you set up SFM, the following are automatically started or enabled: AppleTalk Protocol, File Server for Macintosh, and Print Server for Macintosh.
· The AppleTalk Protocol -- is the layer of AppleTalk Phase 2 protocols that delivers data to its destination on the network. The AppleTalk Protocol can be configured through the Network icon in Control Panel.
· File Server for Macintosh (also called MacFile) -- allows you to designate a directory as a Macintosh-accessible volume, ensures Macintosh filenames are legal NTFS names, and handles permissions. When set up, File Server for Macintosh commands appear in Windows NT Server File Manager and Server Manager under the MacFile menu.
· Print Server for Macintosh (also called MacPrint) -- enables both Windows/DOS and Macintosh clients to send print jobs to either AppleTalk (usually PostScript devices) or non-AppleTalk printing devices. Allows all network users to send print jobs to a spooler on the NT Server and continue working; they need not wait for their print jobs to complete. Windows-based users can also review the print jobs in the Printers folder.
In addition, setting up SFM creates a Control Panel icon that gives you the same server administration capabilities as the MacFile menu (excluding volume management) for the local computer.
The Briefcase and the Directory Replicator service are used to minimize the adminsstation involoved in updating files over network. The Briefcase supports mobile and distributed computing by transparently synchronizing updated files. The Directory Replicator service replicates info such as logon scripts, user profiles, and system policies from a designed export server to one or more import computers.
The NT Briefcase allows users to copy files to their Briefcase, take their Briefcase with them, either on a disk or portable computer, modify the files in the Briefcase, and then on reconnecting to the network, synchronize the files with the original source.
Briefcase can be deployed in any organization where employees spend a significant amount of time working on files off-site. It can also be used to synchronize centrally located files with copies on local computers. In addition, it is possible to have a Briefcase synchronized with files on a network server.
For example, network or mobile users can connect to a file source (or centrally located files), drag files from it to their Briefcase and then work on these files. When the work on the files is complete, the user synchronizes files without having to move the updated file copies out of the Briefcase or manually replace the original files. The Briefcase notes whether either copy of the files has changed, and then updates the unchanged copy. If both copies of the files have changed, Briefcase notes that, but does not automatically update the copies. You can then choose which, if either, file to replace.
The Briefcase Database
The Briefcase Database stores the info required to snychronize files. If it is deleted, it is impossible to synchronize updated files.
The Briefcase Database files are stored in the Briefcase folder, but NOT displayed from NT Explorer. These files may be accessed only from command prompt.
Using the Briefcase
- Files can be copied to the Briefcase throutgh standard methods by a drag-and-drop operation, using Copy and Paste commands, or using the Send to menu command, and so on. (when use Send to menu command, or drag-and-drop operation, to send it to a floppy disk, the Briefcase will disappear from your desktop)
- If you put your Briefcase on a removable media, such as a floppy disk, drag your Briefcase folder back to your desktop. Use the menus in Briefcase to perform the file synchronizations.
NT Directory Replication service is used to maintain identical folder hierarchies, which could include:
- logon scripts -- must be reside on the domain controller that validates the user's logon request.
- system policy files
- commonly used files -- such as online telephone list. These files are typically read-only.
The master directory is maintained on a designated NT Server. Updates made to the files in the master directory are replicated to the other designated computers.
Directory replication makes the same files available at multiple servers. This is useful when a user logs on, because logon scripts must reside on the domain controller that validates the logon. In addition, directory replication helps to balance loads between multiple servers when several users need simultaneous access to file, typically read-only file, thereby avoiding overburdening any one server.
Directory Replication Components
Replicating directory info requires an export server that replicates updated info and one or more import computers that receives a copy of these updated files.
Export /Import Directory and Subdirectories
- The export server keeps the directories to be replicated in a master export directory; by default, it is
(This directory is shared as Repl$ when the Directory Replicator Service is started. )
- Subdirectories under the master export directory must be created by the Administrator for each group of files to be replicated.
- Caution: Files must be placed in subdirectories in the systemroot\System32\Repl\Export directory. Any files placed directly in the directory are NOT replicated.
- Each import computer has an import directory that corresponds to the export server's export directory, by default -- systemroot\System32\Repl\Import. The Directory Replicator service automatically creates subdirectories under this directory to match those on the export server.
- To manage or change the default export or import directory phths, use Server Manager
What computer(s) can be an export server and import computers
- Only an NT Server computer can be an export server.
- NT Server, NT Workstation, and LAN Manager OS/2 server computers can be designated as import computers.
Note: An NT Server that is configured as an export server CAN also be configured as an import computer.
The directory replication process
The Directory Replicator service controls the replication process. Periodically, the export server checks the export directory for changes. If any changes have occurred, --> export server sends update notices to the import computers or domains --> import computer calls the export server and reads the export directory when it receives an update notice -->The import computer copies any new or changed files to its import directory, and deletes any of the import files that are no longer in the export directory.
The parameters that control the Directory Replicators service are located in this registry path:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Replicator\Parameters
Any computer running NT Server can be set up as an export server. (NT Workstation cannot be an export server). Before you set up an export server, you must perform these tasks on the export server:
Create a user account, such as replicator, for the Directory Replicator service to use. This account is added to the domain's Replicator and Backup Operators groups, and all logon hours are allowed. (use User Manager for Domains to create a user account)
From Server Manager >>Computer >>Services >>Directory Replicator, or
>>Control Panel >>Services >>Directory Replicator, configure this service to start automatically and log on as the directory replicator user account.Create/place the directories to be exported. They must be subdirectories of the replication export path, usually C:\systemroot\ System32\Repl\Export.
- From Server Manager, configure the export server to export files to other computers or domains.
- If the import computer is not part of the export server's domain or a trusting domain, create a replicator account (using User Manager for Domains).
This account must have the same name and password as the account used to configure the export server because the account must have permission to access the export server's Repl$ share.
- This account must be a member of the local Replicators and Backup Operators group.
- Use the Directory Replication dialog box to configure the Directory Replicator service to start automatically and to log on as the directory replicator user account.
Directory Replication dialog is accessed either from Server Manger or >>Contorl Panel >>Services
configure the import computer to receive files from other servers or domains, using Server Manager >>double-click the computer >>Replication
Note: On the import computer you do not need to create the import subdirectories. A subdirectory is automatically created the first time it is imported.
Tip: You can set up a server to replicate a directory tree to itself (from its export directory to its import directory). This replication can provide a local backup of the files, or you can use the import version of these files as another source for users to access, while preserving the export version of the files as a source master.
Server Manager is used to configure a server as export server, to specify which computer to export to, and to manage the directories to be exported from the export server.

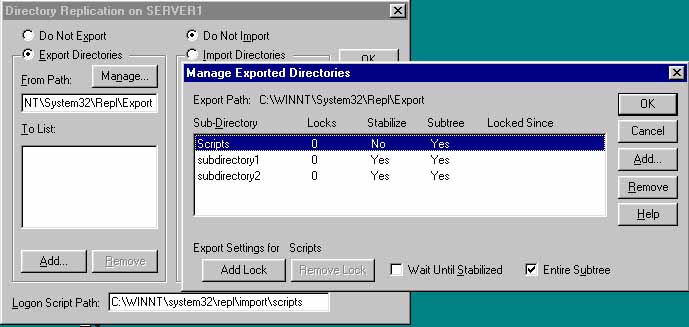
You can lock a subdirectory to prevent it from being exported to any import computers. For example, if you know a directory will be receiving a series of changes that you do not want partially replicated, you can put one or more locks on the subdirectory in the export path. Until you remove the lock or locks, the subdirectory will not be replicated. The date and time the lock was placed is displayed so that you know how long a lock has been in force.
When you stabilize a subdirectory, the export server waits two minutes after changes before exporting the subdirectory. The waiting period allows time for subsequent changes to take place so that all intended changes are recorded before being replicated.
You specify whether the entire subtree (the export subdirectory and all of its subdirectories) or just the first-level subdirectory in the export directory path is exported.
Replicating Logon Scripts -- among DCs only
A logon script is an optional file that runs each time a user logs on. It can be a batch file (.BAT or .CMD filename extension) or an executable program (.EXE filename extension). A logon script path is a local path to the directory where logon scripts are stored.
When a server processes a logon request, the system locates the logon script by combining a file name specified in User Manager for Domains with a path specified in Server Manager (this means all logon scripts must be stored in ONE folder on a DC).
For NT Workstation computers, the logon script path cannot be changed from the default (usually, systemroot\System32\Repl\Import\Scripts)
For a domain, master copies of every logon script should be stored under one replication export directory of one domain controller, either the PDC or a BDC. Copies of these master logon scripts should be replicated to the other servers of the domain. Then, for every other domain controller, the path to imported logon scripts must be entered in Logon script path of the Directory Replication dialog box (->>Servrices...).
If this is done, only one copy of each logon script will need to be maintained, yet every server that participates in authenticating domain logons will have an available, identical copy of all user logon scripts.
Note: The logon script path cannot be administered for NT member server or NT Workstation computers. On these computers, store logon scripts in C:\systemroot\System32\Repl\Import\Scripts or in subdirectories of that path.
Locks -- on an import computer, you can use locks to prevent imports to subdirectories. Locking a subdirectory on an import computer affects replication to only that computer.
Replication of Multiple Directory Trees -- Solution: set up multiple export servers!
Suppose you have a domain where you want to replicate two directory trees -- one for logon scripts and one for other data. The groups of computers that need to import the two trees are different. The four domain controllers need the logon scripts. However, only two of the domain controllers and two NT Workstation computers need to import the other data. The best solution is to set up different servers as the export servers of the scripts directory tree and the data directory tree.
Remember that a single export server has only one list of import computers to which it replicates. If you set up only a single export server for the two directories, it exports both directory trees to all import computers, even though not all import computers use both directory trees.
Note: in a domain, you can have multiple export servers, and an import computer can receive Directory Replication from more than one export servers.
When the Replicator Service generates an error, an event is written to the application log. You view the error using the Event Viewer. Some common problems (as logged in the application log):
Exporting to Specific Computers -- Use Server Manager, make sure that export servers and import computers are specified in the To List and From List, respectively, in the Directory Replication dialog box.
If you do not specify the To List and From List, exporting will occur to all import computers in the local domain, and importing will occur from all export servers in the local domain.
Replication to a Domain Name Over a WAN Link -- Directory replication to a domain name does not always succeed when some or all replication import computers are located across a WAN bridge from an export server. When adding names to the export To List on an export server, and when adding names to the import From List on an import computer, specify the computer names (instead of, or in addition, to specifying the domain name) for those computers separated by a WAN bridge.
Lost Permissions on System32\Repl\Import --Do not use the Explorer or File Manager to examine permissions on the SYSTEM32\REPL\IMPORT directory. If you do, the special permissions initially set there can be lost. These initial permissions enable directory replication to work, and you do not need to change them.
Logon scripts are not working -- On non-domain controller NT Server or NT Workstation computers, store logon scripts in a Scripts folder within the local directory, i.e.:
systemroot\System32\Repl\Import\ScriptsNote: The logon script path CANNOT be administered for NT member Server or for NT Workstation computers (in other words, only domain controllers can be). So you have to store the logon scripts manually. ??
Note: Event Viewer, NT Diagnostics, Performance Monitor can be used for remote computers, as well as local computer.
An event is any potentially significant occurence in the system, or in an application. Event logging starts automatically each time you start an NT computer. With event log and Event Viewer, you can troubleshoot various hardware and software problems and monitor NT security events.
There are three kinds of event logs:
- System log (systemroot\System32\Config\Sysevent.evt) -- events logged by NT system components and device drivers. Such as the failed loading of a driver during startup.
- Application log (systemroot\System32\Config\Appevent.evt) -- events logged by applications.
- Security log (systemroot\System32\Config\Secevent.evt) -- security related events, incl. valid and invalid logon attempts, and events related to resource use, such as creating, opening or deleting files or other objects.
- For example, if you enable Logon and Logoff auditing using User Manager for Domains, attempts to log on to and log off of, the system are recorded in the security log.
- Note:
- -- System and application logs can be viewed by all users; security logs are accessible only to administrators.
- -- By default, security logging is turned off. To enable security logging, run User Manager for Domains to enable auditing and to determine what event to audit.
- Log Files can be saved in one of the three formats:
- Log file format -- for viewing the archived log again in Event Viewer.
- Text file format -- for using the info in an application, such as a word processor.
- Comma-delimited text file format -- for using the info in an application, such as a spreadsheet.
Windows NT Diagnostics (WinMSD.exe in System32 folder) is a recommanded tool to browser a computer's hardware and operating system data stored in the NT registry.
There are 9 tabs on the NT Diagnostics:
Version -- NT version, registered to whom, number of processors installed ...
System -- type of motherboard, CPU, etc.
Display -- info about video adapter
Drives -- info on all of the current installed volumes, grouped by types such as removable drives, hard disks, CD-ROMs, and network drives.
Memory -- how memory is being used in the system. Shows also how much memory are being used by the Kernel and the page file.
Services -- all loaded services and device drivers
Note: to check the dependencies of a service or device driver, click the Dependencies tab (from >>Services >>Properties). For a service or device driver to operate, all of its dependencies must be runing.
Resources -- shows all state of useage of all the hardware in the computer. When viewing Devices, double-click a device will show all the resources that a device is using. To prevent hardware conflicts, review the Resources tab before install new hardware.
Environment -- environment variables that NT uses.
Network -- info about the current network session. The General tab shows which domain or workgroup you are logged into, which account. The Transport tab shows what transport protocols are being used. The Settings shows current network-related settings. The Statistics tab shows network statistics.
Note:
- You cannot edit value entries using Windows NT Diagnostics.
- NT Diagnostics can view either the local NT compter, or a remote NT computer ->>File >>Select computer. (operating system on these computer must be NT!)
Performance Monitor is a graphical tool for measuring the performance of your own computer or other computers on a network. With Permormance Monitor, you can gauge your computer's efficiency, identify and troubleshoot possible problems, and plan for additional hardware needs. You can also alerts to notify you when resource use reaches a specific value.
You can view the behavior of objects, such as processors, memory, cache, threads, and processes on a computer. Each of these objects has an associated set of counters that provide info about device usage, queue lengths, delays, and info used to measure throughput and internal congestion.
It provides charting, alerting, and reporting capabilities that reflect both current activity and ongoing logging. You can open, browse, and chart log files later as if they reflected current activity.
The following overview lists how you use Performance Monitor to view the performance of objects:
- Simultaneously view data or dynamic charts from any number of computers.
- Create, append, export, or view log files containing data about objects on different computers.
- Add system alerts that list events in the Alert Log and notify you either by reverting to Alert view, logging the event in Event Viewer's Application log, or issuing a network alert.
- Run a predefined program either every time or only the first time a counter value goes over or under a user-defined value.
Use Performance Monitor by selecting in this order: --> computers, either local or remote >>objects of a selected computer >>counters of an object for tracking
To create a chart to display performance data in real time:
->Administrative Tools >>Performance Monitor >>View >>Chart, >>Edit >>Add to Chart >>selecet-- Computer, Object(s), Counter(s) >>Add ... >>Done
Three counters for the Processor and System objects are particularly useful for identifying problems:
Processor: % Processor Time -- shows processor activity. If the value of this counter usually falls within 0~80%, with only occasional increase while loading applications, then the processor in probably not slowing down the system or network performance.
Processor: % Interrupt/Sec -- measures the rate of the service requests from I/O devices. A dramatic increase in this value, without a corresponding increase in system activity, shows a hardware problem.
System: Processor Queue Length -- this counter is the instantaneous length of the processor queue in units of threads. A consistent processor queue length greater than two generally indicates processor congestion; the process may be causing problem, the system response/performance is too slow.
Used to capture and display frames (also called packets) in order to detect and troubleshoot problems on LANs. For example, you can use Network Monitor to diagnose hardware and software problems when two or more computers cannot communicate.
To install Network Monitor ->> Control Panel >>Network >>Services >>Add >>Network Monitor Tools and Agent... After installation, it appears on the Administrative Tools (Common) menu.
Network Monitor Agent, available with both NT Server and NT Workstation, simply collects packet info from the network. Remeber Network Monitor Agent CANNOT display or analyze captured info!
Network Monitor Tools, available with only NT Server, display and analyze the captured info.
Features:
For security reasons, Network Monitor captures/displays only those frames sent to or from your computer, including broadcast frames, and multicast frames. It also displays overall network segment statistics for broadcast frames, multicast frames, network utilization, total bytes received per second, and total frames received per second. (Note the difference between "capture" and "display ... statistics for")
To help protect your network from unauthorized use of Network Monitor installations, Network Monitor provides:
- Password protection
The capability to detect other installations of Network Monitor on the local segment of your network. It also detects all instances of the Network Monitor Agent being used remotely (by either Network Monitor from SMS or NT Performance Monitor) to capture data on your network.
Network Monitor can capture only as much info as fits in available system memory. Fortunately, you usually need to capture only a small subset of the frames traveling on your network. To single out a subset of frames, design a capture filter, which functions like a database query. You can filter on the basis of source and destination addresses, protocols, protocol properties, or by specifying a pattern offset.
To have a running capture respond to events on your network as soon as they are detected, design a capture trigger. A capture trigger performs a specified action (such as starting an executable file), when Network Monitor detects a particular set of conditions on the network.
NT allows you to configure the way your system responds to a STOP error (or fatal system error, or blue screen) by using the Recovery utility ->>Control Panel >>System >>Startup/Shutdown >>Recovery:
Recovery When a STOP error occurs, do the following:
Write an event to the system log
Send an administrative alert
Write debugging information to
Overwrite any existing file
Automatically reboot
Notes and Tips
- You must be logged on as an Administrator to change Recovery options.
- Write an event to the system log, Send an administrative alert, and Automatically reboot require at least a 2 MB paging file on the system drive.
Users and computers for Send an administrative alert to are specified using >>Server Manager >>Computer >>Properties >>Alerts
- Write debugging information to requires a paging file on the system drive at least as large as the physical memory (or physical RAM + 1 MB). (note: size and location of the pagefile)
(Reason: a program named Savedump.exe dump/write the entire contents of memory to the pagefile, if a STOP error occurs and this option was selected)
The memory.dmp file can be viewed with DumpExam.exe utility
NT always writes the dump file to the same filename (by default, the file is %SystemRoot%\Memory.dmp). To keep dump files, copy them to a new filename after each STOP error.
- You can save some memory if you clear these options: Write debugging information to, Write an event to the system log, or Send an administrative alert. The memory saved depends on the computer, but typically is about 60-70K required by the drivers that enable these features.
Only clearing Automatically reboot does NOT save memory; clearing all other three options do.
i.e. the MBR is damaged -- use MS-DOS utility FDISK and issuing teh command at the C:\> prompt: fdisk /mbr
With the /mbr switch, FDISK will write a new master boot record to the hard disk. You may see this problem if you turn off sector translation in the BIOS of your hard disk controller. Try changing sector translation setting before issuing this command.
This command will not have an adverse effect on your system -- even if it doesn't correct the problem.
You have to create new partitions, format them and reinstall NT
STOP: 0x0000007E: Inaccessible Boot Device
Problem: The NT loader cannot access the hard disk. Some SCSI adapters do not conform to the complete SCSI standard may cause this problem.
Solution: If you have just added a SCSI controller to an NT computer that boots from an IDE hard disk, make sure no SCSI device is set to id 0 (or otherwise disable bootable SCSI hard disks). If not, the boot.ini would refers to the wrong partition number.
The Emergency Repair Disk (ERD) stores mainly some of the configuration info of the Registry, it can be used to (partially) restore the Registry.
Rdisk.exe is used to create or update the ERD.
ERD includes the SAM (Security Account Manager) database, disk configuration, and numerous other system parameters.
To perform an ER, you need to use the 3 NT Startup floppies, ERD and probaly, the installation CD.
When performing an ER process, you can choose if to restore any of the registry hives that are stored in ERD.
The NT Boot Disk, as it contains only 3~5 NT boot files (Ntldr, Ntdetect.com, boot.ini, and maybe also Ntbootdd.sys, bootsect.sys) which are at the root of NT system partition, can only be used to fix simple problem related to corrupted/missing boot files, or wrong ARC path in boot.ini.
More severe problem, such as missing/corrupt system files in the boot partition, or damaged Resgistry configuration, the Boot Disk will be of no use. You can use the ERD to perform a repair process in these cases.
The NT utility Dr. Watson is specially for troubleshooting application, it automatically detects, diagnoses, and logs application errors (in binary crash dump files).
To configure Dr. Watson for using specific parameters, run DrWtsn32.exe command.
Recordes that Dr. Watson generates are, by default:
- User.dmp -- a binary crash dump file, which can be viewed with Windows Debugger
- Drwtsn32.log -- a log file containing the diagnostic info about application errors
- an entry in the Event Viewer’s Application Log
For more info on Dr. Watson for NT, click here
Memory.dmp and User.dmp
Memory.dmp is generated when a STOP (a.k.a. the blue screen) error occurs, which is caused by NT sytem failure(s). You specify it via >>Control Panel >>System >>Starup/Shutdown tab >Recovey. Contents of Memory.dmp can be viewed with the DumpExam.exe utility.
User.dmp is generated by Dr.Watson from application errors; it's a binary dump file which can be loaded into Windows Debugger
Both the dump files are all located in the systemroot (typically the C:\Winnt folder) by default.
Why -- the resource, e.g. a directory/file, was created and assigned permissions under a previous installation of NT that has been overwritten (NOT during a upgrading). Now the old administrator account that no longer exists is the owner. Because NT assigns a new security ID to the new administrator during the new installation, no current user has the permission to use or delete the resource.
Solution -- an administrator can take ownership of it and then reassign permissions as necessary.